“All warfare is based on deception. — Sun Tzu”
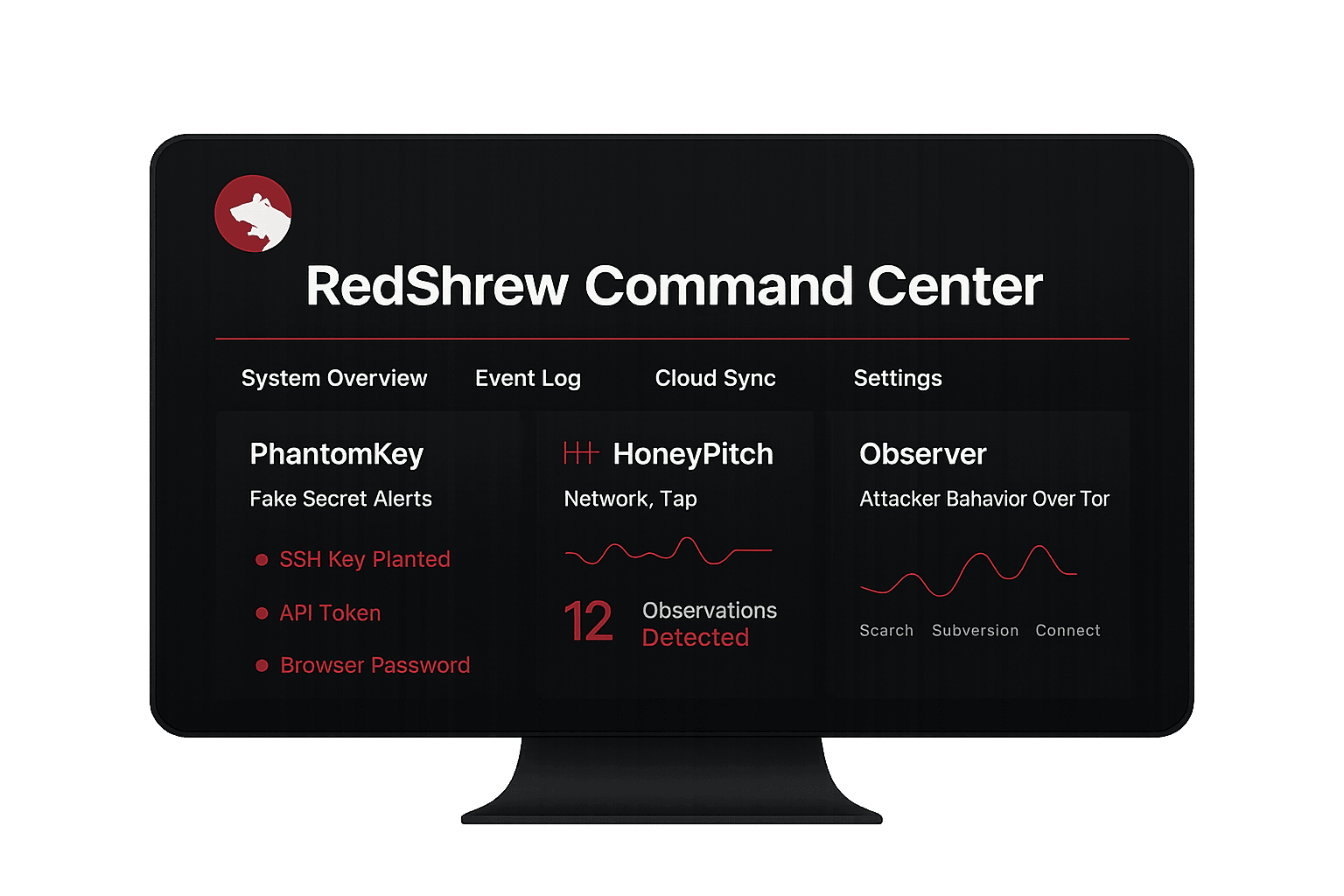
When an attack happens, respond faster with RedShrew
Deception-Driven Threat Detection
Honeypot Traps
Instantly surface attacker actions that matter most. Deceive, observe, and triage intrusions in real time, no more alert fatigue.
Rewind every move made by adversaries. Follow their path from the first scan to their last attempt at lateral movement.
Block, mislead, or monitor attackers on autopilot. Trigger custom responses, alerts, or forensics as soon as traps are touched.
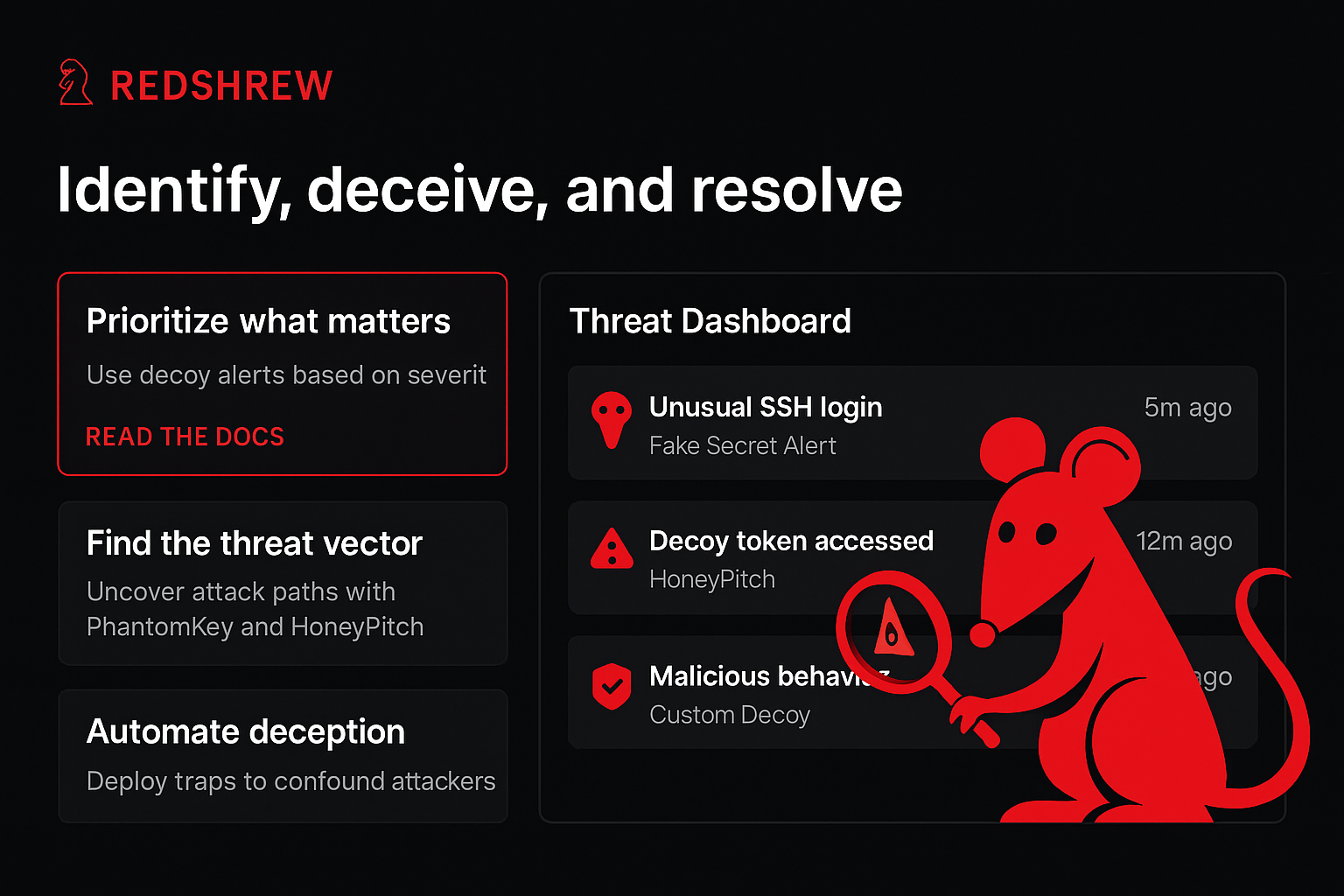
Attack Tracing
Don’t just observe.
Take action.
See the complete trace path from breach to bottleneck. Map attacker routes and service disruptions across your entire system.
Identify network or system areas where attackers repeatedly fail or succeed. Use trace telemetry to dynamically reinforce weak points.
Detect repeating exploit attempts and adversary behavior using historical trace patterns. Optimize defenses based on real TTPs.
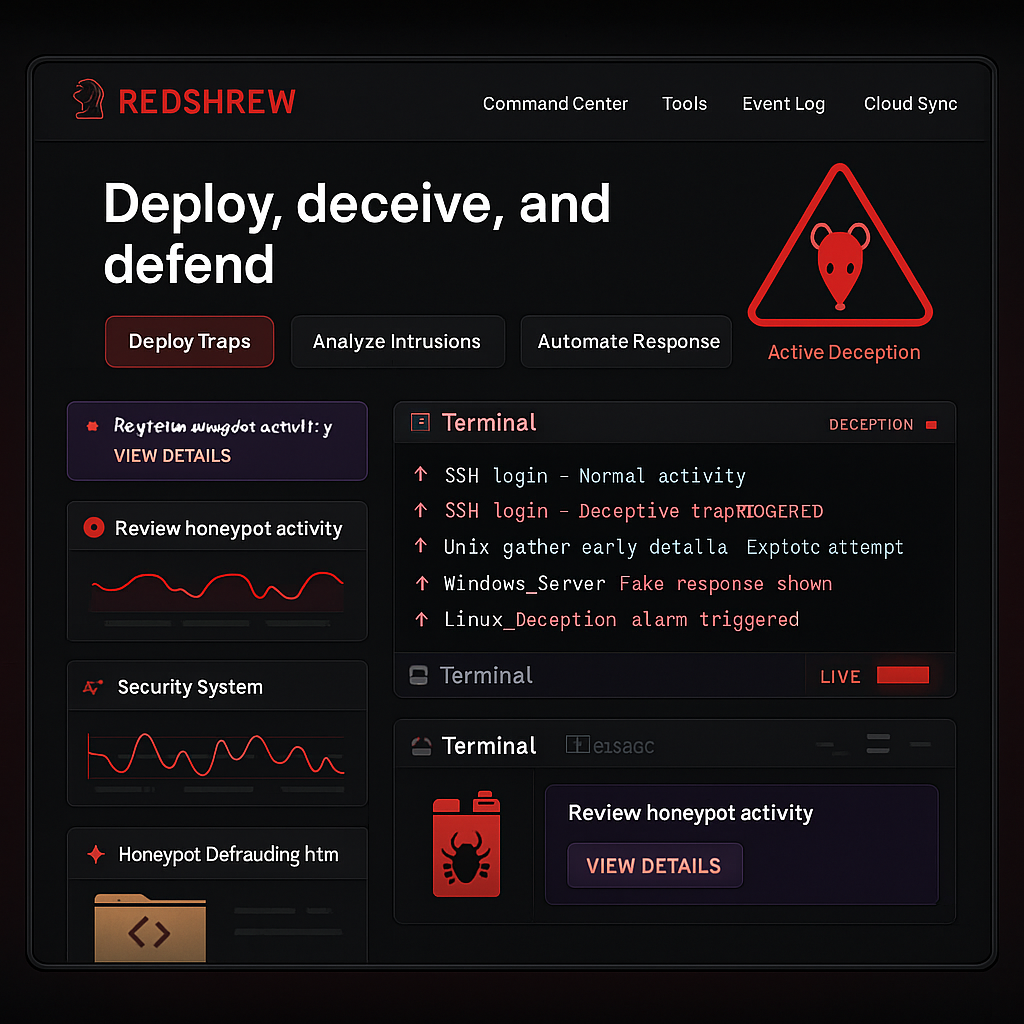
Deploy in Seconds
RedShrew works with every major platform and technology stack.
Drop RedShrew into your stack. Arm your systems with deception traps instantly.
import * as RedShrew from '@redshrew/nextjs';
RedShrew.init({
dsn: 'https://yourRedshrewKey@redshrew.com/ingest',
deception: true,
traps: [ 'ssh', 'api', 'browser' ],
alertSampleRate: 1.0
});Get the Latest from RedShrew
Sign up for exclusive deception ops, threat research, and product news.
We don’t spam. Just smart, monthly updates—maybe the occasional urgent threat alert, but never daily noise.
Of course we have more content
Outsmart Threats Before They Strike.
Deploy the only deception platform that empowers defenders to catch, mislead, and study adversaries without slowing down real operations.






